Windows Servicing Identified That Package Update Is Not Applicable For This System Rating: 9,1/10 3152votes
EULA Enterprise WDKINSTALLATION AND USE RIGHTS. Installation and use. End user license agreement for the Enterprise Windows Driver Kit EWDK. One user may install and use any number of copies of the software on your devices to design, develop and test your programs. Further, you may install, use andor deploy via a network management system or as part of a desktop image, any number of copies of the software on computer devices within your internal corporate network to design, develop and test your programs that run on a Microsoft operating system. Each copy must be complete, including all copyright and trademark notices. You must require end users to agree to terms that protect the software as much as these license terms. Included Microsoft Programs. Windows Servicing Identified That Package Update Is Not Applicable For This System' title='Windows Servicing Identified That Package Update Is Not Applicable For This System' />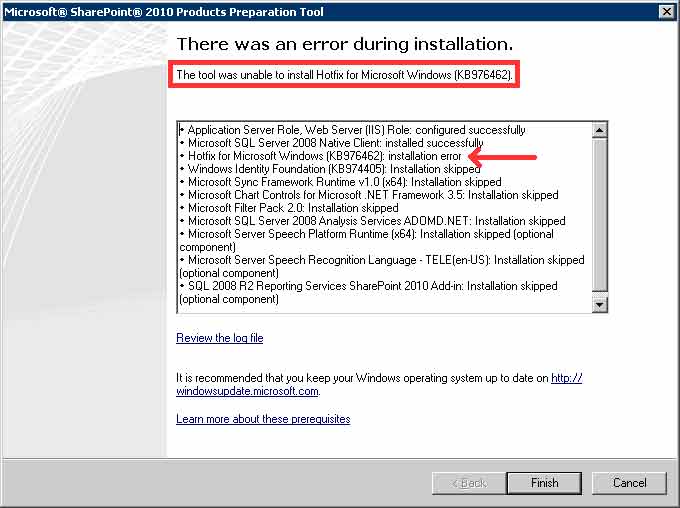 The software contains other Microsoft programs. These license terms govern your use of included Microsoft programs. Utilities. The software contains certain components that are identified in the Utilities List located. Link. Id5. 24. 83. Depending on the specific edition of the software, the number of Utility files you receive with the software may not be equal to the number of Utilities listed in the Utilities List. Except as otherwise provided on the Utilities List for specific files, you may copy and install the Utilities you receive with the software on to other third party machines. These Utilities may only be used to debug and deploy your programs and databases you have developed with the software. You must delete all the Utilities installed onto a third party machine within the earlier of i when you have finished debugging or deploying your programs or ii thirty 3. Utilities onto that machine. We may add additional files to this list from time to time. Build Server List. The software contains certain components that are identified in the Build Server List located at. Link. Id5. 24. 83. Fud/FileDownloadHandler.ashx?fid=6f0de65b-d6a7-4912-afde-f071e22e9771' alt='Windows Servicing Identified That Package Update Is Not Applicable For This System' title='Windows Servicing Identified That Package Update Is Not Applicable For This System' />You may install copies of the files listed in it, onto your build machines, solely for the purpose of compiling, building, verifying and archiving your programs. These components may only be used in order to create and configure build systems internal to your organization to support your internal build environment. These components do not provide external distribution rights to any of the software or enable you to provide a build environment as a service to third parties. We may add additional files to this list from time to time. This section of the documentation provides specifications for hardware compatibility for systems running Windows 10, version 1607. System. Client. BluetoothController. Base. View and Download Ford EDGE 2013 owners manual online. EDGE 2013 Automobile pdf manual download. View and Download Ford 2014 Super Duty owners manual online. Ford Super Duty. 2014 Super Duty Automobile pdf manual download. The servicing stack includes the files and resources that are required to service a Windows image. This includes the Package Manager executable, the required. Third Party Programs. The software may include third party code that Microsoft, not the third party, licenses to you under this agreement. Notices, if any, for the third party code are included for your information only and may be found in the credits. Third. Party. Notices. ADDITIONAL LICENSING REQUIREMENTS ANDOR USE RIGHTS. Distributable Code. The software contains code that you are permitted to distribute in programs you develop if you comply with the terms below. Right to Use and Distribute. The code and text files listed below are Distributable Code. REDIST. 3. Search for Windows Update service, then right click on it and select Stop. Navigate to CWindows folder. Delete or rename e. Are you a new entrant Are you new to interstate commerce Have you been notified that you are subject to a New Entrant Safety Audit SAM. The System for Award Management SAM is the Official U. S. Government system that consolidated the capabilities of CCRFedReg, ORCA, and EPLS. Federal government web portal for veteran owned businesses. Supports the implementation of the Veterans Entrepreneurship and Small Business Development Act of 1999. Home News Archive. News Archive. 2017 October October 26, 2017 Knowledge Center PCL inquiries closed Oct. Personnel Security PCL inquiries Option 2. TXT Files. You may copy and distribute the object code form of code listed in REDIST. TXT files plus any of the files listed on the REDIST list located at. Link. Id2. 94. 84. Third party distribution. You may permit distributors of your programs to copy and distribute the Distributable Code as part of those programs. Distribution Requirements. For any Distributable Code you distribute, you mustadd significant primary functionality to it in your programs for any Distributable Code having a filename extension of. Distributable Code through a linker with your program distribute Distributable Code included in a setup program only as part of that setup program without modification require distributors and external end users to agree to terms that protect it at least as much as this agreement display your valid copyright notice on your programs andindemnify, defend, and hold harmless Microsoft from any claims, including attorneys fees, related to the distribution or use of your programs. Distribution Restrictions. You may notalter any copyright, trademark or patent notice in the Distributable Code use Microsofts trademarks in your programs names or in a way that suggests your programs come from or are endorsed by Microsoft distribute Distributable Code to run on a platform other than the Windows platform include Distributable Code in malicious, deceptive or unlawful programs ormodify or distribute the source code of any Distributable Code so that any part of it becomes subject to an Excluded License. An Excluded License is one that requires, as a condition of use, modification or distribution, that the code be disclosed or distributed in source code form orothers have the right to modify it. Distribution Rights for Features made Available with the Software. Windows App Requirements. If you intend to make your program available in the Microsoft Store, the program must comply with the Certification as defined and described in the App Developer Agreement, currently available at msdn. Bing Maps. The software may include features that retrieve content such as maps, images, and other data through the Bing Maps or successor branded application programming interface the Bing Maps API to create reports displaying data on top of maps, aerial and hybrid imagery. If these features are included, you may use these features to create and view dynamic or static documents only in conjunction with and through methods and means of access integrated in the software. You may not otherwise copy, store, archive, or create a database of the entity information including business names, addresses and geocodes available through the Bing Maps API. You may not use the Bing Maps API to provide sensor based guidancerouting, nor use any Road Traffic Data or Birds Eye Maps API and associated content is also subject to the additional terms and conditions at. Link. ID2. 19. 69. Additional Mapping APIs. The software may include application programming interfaces that provide maps and other related mapping features and services that are not provided by Bing the Additional Mapping APIs. These Additional Mapping APIs are subject to additional terms and conditions and may require payment of fees to Microsoft andor third party providers based on the use or volume of use of such Additional Mapping APIs. These terms and conditions will be provided when you obtain any necessary license keys to use such Additional Mapping APIs or when you review or receive documentation related to the use of such Additional Mapping APIs. Push Notifications. The Microsoft Push Notification Service may not be used to send notifications that are mission critical or otherwise could affect matters of life or death, including without limitation critical notifications related to a medical device or condition. MICROSOFT EXPRESSLY DISCLAIMS ANY WARRANTIES THAT THE USE OF THE MICROSOFT PUSH NOTIFICATION SERVICE OR DELIVERY OF MICROSOFT PUSH NOTIFICATION SERVICE NOTIFICATIONS WILL BE UNINTERRUPTED, ERROR FREE, OR OTHERWISE GUARANTEED TO OCCUR ON A REAL TIME BASIS. Speech namespace API. Using speech recognition functionality via the Speech namespace APIs in a program requires the support of a speech recognition service. The service may require network connectivity at the time of recognition e. In addition, the service may also collect speech related data in order to provide and improve the service. The speech related data may include, for example, information related to grammar size and string phrases in a grammar. Oracle Critical Patch Update October 2. Appendix Oracle Database Server. Oracle Database Server Executive Summary. This Critical Patch Update contains 1. Oracle Database Server divided as follows 9 new security fixes for the Oracle Database Server. Oracle Database Server installed. The English text form of this Risk Matrix can be found here. Oracle Secure Backup. Both of these vulnerabilities may be remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Big Data Graph. This vulnerability is not remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Database Server Risk Matrix. CVEComponent. Package andor Privilege Required. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 6 5. OJVMCreate Session, Create Procedure. Multiple. No. 9. 1. Network. Low. High. None. Changed. High. High. High. 11. 2. CVE 2. 01. 6 5. Kernel PDBCreate Session. Oracle Net. No. 6. Local. High. High. None. Un changed. High. High. High. CVE 2. 01. 6 5. RDBMS Security. Create Session. Oracle Net. No. 6. Local. High. High. None. Un changed. High. High. High. CVE 2. 01. 0 5. Application Express. None. HTTPYes. 6. Network. Low. None. Required. Changed. Low. Low. None. Prior to 5. CVE 2. 01. 6 5. Kernel PDBExecute on DBMSPDBEXECSQLOracle Net. No. 6. 0. Local. Low. High. None. Changed. None. None. High. CVE 2. 01. 6 5. RDBMS Programmable Interface. Create Session. Oracle Net. No. 5. 5. Local. Low. Low. None. Un changed. High. None. None. CVE 2. 01. 6 5. RDBMS Security. Create Session. Oracle Net. No. 3. Local. Low. Low. None. Un changed. Low. None. None. 11. CVE 2. 01. 6 5. RDBMS Security. Create Session. Oracle Net. No. 3. Local. Low. Low. None. Un changed. Low. None. None. 11. CVE 2. 01. 6 3. RDBMS Security and SQLlus. DBA level privileged account. Oracle Net. No. 2. Network. Low. High. Required. Un changed. Low. None. None. 11. See Note 1. Notes Fix applicable to both server and client side installations. Oracle Database Server Client Only Installations. The following Oracle Database Server vulnerability included in this Critical Patch Update affects client only installations CVE 2. Oracle Secure Backup Executive Summary. This Critical Patch Update contains 2 new security fixes for Oracle Secure Backup. Both of these vulnerabilities may be remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Secure Backup Risk Matrix. CVEComponent. Package andor Privilege Required. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 5 1. Oracle Secure Backup. None. Multiple. Yes. Network. Low. None. None. Changed. None. None. Low. Prior to 1. CVE 2. 01. 5 0. Oracle Secure Backup. None. SSLYes. 5. 8. Network. Low. None. None. Changed. None. None. Low. Prior to 1. Oracle Big Data Graph Executive Summary. This Critical Patch Update contains 1 new security fix for Oracle Big Data Graph. This vulnerability is not remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Big Data Graph Risk Matrix. CVEComponent. Sub component. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Bijoy 52 Bangla Software Free Download Windows 8. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 5 7. Big Data Graph. Apache Commons Collections. HTTPNo. 8. 8. Network. Low. Low. None. Un changed. High. High. High. Prior to 1. 2. Appendix Oracle Fusion Middleware. Oracle Fusion Middleware Executive Summary. This Critical Patch Update contains 2. Oracle Fusion Middleware. The English text form of this Risk Matrix can be found here. Oracle Fusion Middleware products include Oracle Database components that are affected by the vulnerabilities listed in the Oracle Database section. The exposure of Oracle Fusion Middleware products is dependent on the Oracle Database version being used. Oracle Database security fixes are not listed in the Oracle Fusion Middleware risk matrix. However, since vulnerabilities affecting Oracle Database versions may affect Oracle Fusion Middleware products, Oracle recommends that customers apply the October 2. Critical Patch Update to the Oracle Database components of Oracle Fusion Middleware products. For information on what patches need to be applied to your environments, refer to Critical Patch Update October 2. Patch Availability Document for Oracle Products, My Oracle Support Note 2. Oracle Fusion Middleware Risk Matrix. CVEComponent. Sub component. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 5 3. Oracle Big Data Discovery. Data Processing. HTTPYes. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 3. Oracle Web Services. JAXWS Web Services Stack. HTTPYes. 9. 8. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 5 7. Oracle Web. Logic Server. None. HTTPYes. 9. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 5. Oracle Web. Logic Server. None. HTTPYes. 9. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 5. Oracle Web. Logic Server. WLS Web. Services. HTTPYes. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 1. Oracle Glass. Fish Server. Security. HTTPSYes. Network. Low. None. Required. Un changed. High. High. High. CVE 2. Oracle Glass. Fish Server. Java Server Faces. Multiple. No. 8. 8. Network. Low. Low. None. Un changed. High. High. High. CVE 2. 01. 6 3. Oracle Web. Logic Server. Java. Server Faces. HTTPNo. Network. Low. Low. None. Un changed. High. High. High. CVE 2. 01. 6 1. Oracle i. Planet Web Proxy Server. Security. HTTPSYes. Network. Low. None. Required. Un changed. High. High. High. CVE 2. 01. 6 1. Oracle i. Planet Web Server. Security. HTTPSYes. Network. Low. None. Required. Un changed. High. High. High. CVE 2. 01. 6 5. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. BI Publisher formerly XML PublisherSecurity. HTTPNo. 7. 7. Network.
The software contains other Microsoft programs. These license terms govern your use of included Microsoft programs. Utilities. The software contains certain components that are identified in the Utilities List located. Link. Id5. 24. 83. Depending on the specific edition of the software, the number of Utility files you receive with the software may not be equal to the number of Utilities listed in the Utilities List. Except as otherwise provided on the Utilities List for specific files, you may copy and install the Utilities you receive with the software on to other third party machines. These Utilities may only be used to debug and deploy your programs and databases you have developed with the software. You must delete all the Utilities installed onto a third party machine within the earlier of i when you have finished debugging or deploying your programs or ii thirty 3. Utilities onto that machine. We may add additional files to this list from time to time. Build Server List. The software contains certain components that are identified in the Build Server List located at. Link. Id5. 24. 83. Fud/FileDownloadHandler.ashx?fid=6f0de65b-d6a7-4912-afde-f071e22e9771' alt='Windows Servicing Identified That Package Update Is Not Applicable For This System' title='Windows Servicing Identified That Package Update Is Not Applicable For This System' />You may install copies of the files listed in it, onto your build machines, solely for the purpose of compiling, building, verifying and archiving your programs. These components may only be used in order to create and configure build systems internal to your organization to support your internal build environment. These components do not provide external distribution rights to any of the software or enable you to provide a build environment as a service to third parties. We may add additional files to this list from time to time. This section of the documentation provides specifications for hardware compatibility for systems running Windows 10, version 1607. System. Client. BluetoothController. Base. View and Download Ford EDGE 2013 owners manual online. EDGE 2013 Automobile pdf manual download. View and Download Ford 2014 Super Duty owners manual online. Ford Super Duty. 2014 Super Duty Automobile pdf manual download. The servicing stack includes the files and resources that are required to service a Windows image. This includes the Package Manager executable, the required. Third Party Programs. The software may include third party code that Microsoft, not the third party, licenses to you under this agreement. Notices, if any, for the third party code are included for your information only and may be found in the credits. Third. Party. Notices. ADDITIONAL LICENSING REQUIREMENTS ANDOR USE RIGHTS. Distributable Code. The software contains code that you are permitted to distribute in programs you develop if you comply with the terms below. Right to Use and Distribute. The code and text files listed below are Distributable Code. REDIST. 3. Search for Windows Update service, then right click on it and select Stop. Navigate to CWindows folder. Delete or rename e. Are you a new entrant Are you new to interstate commerce Have you been notified that you are subject to a New Entrant Safety Audit SAM. The System for Award Management SAM is the Official U. S. Government system that consolidated the capabilities of CCRFedReg, ORCA, and EPLS. Federal government web portal for veteran owned businesses. Supports the implementation of the Veterans Entrepreneurship and Small Business Development Act of 1999. Home News Archive. News Archive. 2017 October October 26, 2017 Knowledge Center PCL inquiries closed Oct. Personnel Security PCL inquiries Option 2. TXT Files. You may copy and distribute the object code form of code listed in REDIST. TXT files plus any of the files listed on the REDIST list located at. Link. Id2. 94. 84. Third party distribution. You may permit distributors of your programs to copy and distribute the Distributable Code as part of those programs. Distribution Requirements. For any Distributable Code you distribute, you mustadd significant primary functionality to it in your programs for any Distributable Code having a filename extension of. Distributable Code through a linker with your program distribute Distributable Code included in a setup program only as part of that setup program without modification require distributors and external end users to agree to terms that protect it at least as much as this agreement display your valid copyright notice on your programs andindemnify, defend, and hold harmless Microsoft from any claims, including attorneys fees, related to the distribution or use of your programs. Distribution Restrictions. You may notalter any copyright, trademark or patent notice in the Distributable Code use Microsofts trademarks in your programs names or in a way that suggests your programs come from or are endorsed by Microsoft distribute Distributable Code to run on a platform other than the Windows platform include Distributable Code in malicious, deceptive or unlawful programs ormodify or distribute the source code of any Distributable Code so that any part of it becomes subject to an Excluded License. An Excluded License is one that requires, as a condition of use, modification or distribution, that the code be disclosed or distributed in source code form orothers have the right to modify it. Distribution Rights for Features made Available with the Software. Windows App Requirements. If you intend to make your program available in the Microsoft Store, the program must comply with the Certification as defined and described in the App Developer Agreement, currently available at msdn. Bing Maps. The software may include features that retrieve content such as maps, images, and other data through the Bing Maps or successor branded application programming interface the Bing Maps API to create reports displaying data on top of maps, aerial and hybrid imagery. If these features are included, you may use these features to create and view dynamic or static documents only in conjunction with and through methods and means of access integrated in the software. You may not otherwise copy, store, archive, or create a database of the entity information including business names, addresses and geocodes available through the Bing Maps API. You may not use the Bing Maps API to provide sensor based guidancerouting, nor use any Road Traffic Data or Birds Eye Maps API and associated content is also subject to the additional terms and conditions at. Link. ID2. 19. 69. Additional Mapping APIs. The software may include application programming interfaces that provide maps and other related mapping features and services that are not provided by Bing the Additional Mapping APIs. These Additional Mapping APIs are subject to additional terms and conditions and may require payment of fees to Microsoft andor third party providers based on the use or volume of use of such Additional Mapping APIs. These terms and conditions will be provided when you obtain any necessary license keys to use such Additional Mapping APIs or when you review or receive documentation related to the use of such Additional Mapping APIs. Push Notifications. The Microsoft Push Notification Service may not be used to send notifications that are mission critical or otherwise could affect matters of life or death, including without limitation critical notifications related to a medical device or condition. MICROSOFT EXPRESSLY DISCLAIMS ANY WARRANTIES THAT THE USE OF THE MICROSOFT PUSH NOTIFICATION SERVICE OR DELIVERY OF MICROSOFT PUSH NOTIFICATION SERVICE NOTIFICATIONS WILL BE UNINTERRUPTED, ERROR FREE, OR OTHERWISE GUARANTEED TO OCCUR ON A REAL TIME BASIS. Speech namespace API. Using speech recognition functionality via the Speech namespace APIs in a program requires the support of a speech recognition service. The service may require network connectivity at the time of recognition e. In addition, the service may also collect speech related data in order to provide and improve the service. The speech related data may include, for example, information related to grammar size and string phrases in a grammar. Oracle Critical Patch Update October 2. Appendix Oracle Database Server. Oracle Database Server Executive Summary. This Critical Patch Update contains 1. Oracle Database Server divided as follows 9 new security fixes for the Oracle Database Server. Oracle Database Server installed. The English text form of this Risk Matrix can be found here. Oracle Secure Backup. Both of these vulnerabilities may be remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Big Data Graph. This vulnerability is not remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Database Server Risk Matrix. CVEComponent. Package andor Privilege Required. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 6 5. OJVMCreate Session, Create Procedure. Multiple. No. 9. 1. Network. Low. High. None. Changed. High. High. High. 11. 2. CVE 2. 01. 6 5. Kernel PDBCreate Session. Oracle Net. No. 6. Local. High. High. None. Un changed. High. High. High. CVE 2. 01. 6 5. RDBMS Security. Create Session. Oracle Net. No. 6. Local. High. High. None. Un changed. High. High. High. CVE 2. 01. 0 5. Application Express. None. HTTPYes. 6. Network. Low. None. Required. Changed. Low. Low. None. Prior to 5. CVE 2. 01. 6 5. Kernel PDBExecute on DBMSPDBEXECSQLOracle Net. No. 6. 0. Local. Low. High. None. Changed. None. None. High. CVE 2. 01. 6 5. RDBMS Programmable Interface. Create Session. Oracle Net. No. 5. 5. Local. Low. Low. None. Un changed. High. None. None. CVE 2. 01. 6 5. RDBMS Security. Create Session. Oracle Net. No. 3. Local. Low. Low. None. Un changed. Low. None. None. 11. CVE 2. 01. 6 5. RDBMS Security. Create Session. Oracle Net. No. 3. Local. Low. Low. None. Un changed. Low. None. None. 11. CVE 2. 01. 6 3. RDBMS Security and SQLlus. DBA level privileged account. Oracle Net. No. 2. Network. Low. High. Required. Un changed. Low. None. None. 11. See Note 1. Notes Fix applicable to both server and client side installations. Oracle Database Server Client Only Installations. The following Oracle Database Server vulnerability included in this Critical Patch Update affects client only installations CVE 2. Oracle Secure Backup Executive Summary. This Critical Patch Update contains 2 new security fixes for Oracle Secure Backup. Both of these vulnerabilities may be remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Secure Backup Risk Matrix. CVEComponent. Package andor Privilege Required. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 5 1. Oracle Secure Backup. None. Multiple. Yes. Network. Low. None. None. Changed. None. None. Low. Prior to 1. CVE 2. 01. 5 0. Oracle Secure Backup. None. SSLYes. 5. 8. Network. Low. None. None. Changed. None. None. Low. Prior to 1. Oracle Big Data Graph Executive Summary. This Critical Patch Update contains 1 new security fix for Oracle Big Data Graph. This vulnerability is not remotely exploitable without authentication, i. The English text form of this Risk Matrix can be found here. Oracle Big Data Graph Risk Matrix. CVEComponent. Sub component. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Bijoy 52 Bangla Software Free Download Windows 8. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 5 7. Big Data Graph. Apache Commons Collections. HTTPNo. 8. 8. Network. Low. Low. None. Un changed. High. High. High. Prior to 1. 2. Appendix Oracle Fusion Middleware. Oracle Fusion Middleware Executive Summary. This Critical Patch Update contains 2. Oracle Fusion Middleware. The English text form of this Risk Matrix can be found here. Oracle Fusion Middleware products include Oracle Database components that are affected by the vulnerabilities listed in the Oracle Database section. The exposure of Oracle Fusion Middleware products is dependent on the Oracle Database version being used. Oracle Database security fixes are not listed in the Oracle Fusion Middleware risk matrix. However, since vulnerabilities affecting Oracle Database versions may affect Oracle Fusion Middleware products, Oracle recommends that customers apply the October 2. Critical Patch Update to the Oracle Database components of Oracle Fusion Middleware products. For information on what patches need to be applied to your environments, refer to Critical Patch Update October 2. Patch Availability Document for Oracle Products, My Oracle Support Note 2. Oracle Fusion Middleware Risk Matrix. CVEComponent. Sub component. Protocol. Remote. Exploitwithout. Auth. CVSS VERSION 3. 0 RISK see Risk Matrix DefinitionsSupported Versions Affected. Notes. Base. Score. Attack. Vector. Attack. Complex. Privs. Reqd. User. Interact. Scope. Confid entiality. Inte grity. Avail ability. CVE 2. 01. 5 3. Oracle Big Data Discovery. Data Processing. HTTPYes. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 3. Oracle Web Services. JAXWS Web Services Stack. HTTPYes. 9. 8. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 5 7. Oracle Web. Logic Server. None. HTTPYes. 9. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 5. Oracle Web. Logic Server. None. HTTPYes. 9. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 5. Oracle Web. Logic Server. WLS Web. Services. HTTPYes. Network. Low. None. None. Un changed. High. High. High. CVE 2. 01. 6 1. Oracle Glass. Fish Server. Security. HTTPSYes. Network. Low. None. Required. Un changed. High. High. High. CVE 2. Oracle Glass. Fish Server. Java Server Faces. Multiple. No. 8. 8. Network. Low. Low. None. Un changed. High. High. High. CVE 2. 01. 6 3. Oracle Web. Logic Server. Java. Server Faces. HTTPNo. Network. Low. Low. None. Un changed. High. High. High. CVE 2. 01. 6 1. Oracle i. Planet Web Proxy Server. Security. HTTPSYes. Network. Low. None. Required. Un changed. High. High. High. CVE 2. 01. 6 1. Oracle i. Planet Web Server. Security. HTTPSYes. Network. Low. None. Required. Un changed. High. High. High. CVE 2. 01. 6 5. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. Oracle Outside In Technology. Outside In Filters. HTTPYes. 8. 6. Network. Low. None. None. Un changed. High. Low. Low. 8. See Note 1. CVE 2. BI Publisher formerly XML PublisherSecurity. HTTPNo. 7. 7. Network.
