Universal VPN Client software for highly secure remote connectivity. VPN Overview. What is a VPNThis stepbystep guide explains how to install and configure public key infrastructure, based on Windows 2012 R2 Server core offline Root CA Windows 2012 R2. Microsoft isnt messing around when it comes to phones anymore Windows Phone 7 doesnt just catch up with Android and the iPhone in many ways it surpassed those. UQbx4K_xg/UbXTaxXB1xI/AAAAAAAABD8/1OSOSlEiFh8/s430/windows-7-features-large.jpg' alt='Client For Microsoft Networks Windows 7 Inf' title='Client For Microsoft Networks Windows 7 Inf' />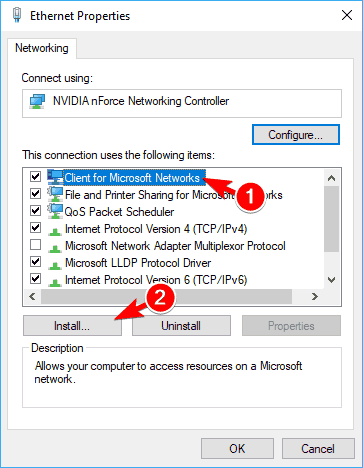 A RIS Disc image went out that did not have File and Print Sharing for Microsoft Networks turned on Oh NO Now I want to fix it with a script deployed. This article shows how make Cisco VPN Client work with Windows 8 32bit 64bit. VPN Client including 5. VPN networks due. Component Description Supported by Active Directory A set of technologies introduced with Windows 2000 that allows administrators to assign enterprisewide policies. Client For Microsoft Networks Windows 7 Info' title='Client For Microsoft Networks Windows 7 Info' />A virtual private network VPN is a way to use a public telecommunication infrastructure. Internet, to provide remote offices or individual users with secure access to. In the past, companies would have rented expensive systems of leased lines to build. VPN only they could use. A VPN provides the same capabilities at a much lower cost. A VPN works by using the Internet while maintaining privacy through security procedures and. Windows 98 codenamed Memphis while in development is a graphical operating system by Microsoft. It is the second major release in the Windows 9x line of operating. Layer Two Tunneling Protocol L2. TP or IPSec. In effect, private data. Why IPSec is strong Definition IPSec Internet Protocol Security provides security services at the IP layer. The IPsec architecture is described in the RFC 2. RFC 2. 40. 1. IPSec has been selected to be embedded in IPv. IPSec is strong because it was designed to be. PPTP. Today IPSec is the most secure way to access the corporate network from the Internet, here are some elements why Strong encryption mechanisms like Encapsulated Security Payload ESP using DES, 3. DES, AES with long key length i. Strong authentication of parties identity with the use of X Auth and Certificate with long key length i. Use of Internet Key Exchange IKE and ISAKMP to automatically exchange keys and mutual authentication. Protection against denial of service attacks. The IPSec protocols use a sliding window. Packets are numbered and only accepted if they fit the window. Use of USB Stick, USB Token in conjunction with IPSec Client software to protect identityauthentication information and VPN configurations i. The. Green. Bow specific feature. What is NAT Traversal and do you support itDefinition Network Address Translation NAT is designed to decrease IT manager frustration for. IP addresses. A NAT device takes a packets originating private IP address. IP address, before sending the packet across the Internet. NAT devices use an internal table to keep track of translated addresses but. IP header, impacting IPSec ability to function. IETF Internet Engineering Task Force group worked out a solution called NAT Traversal. NAT T RFC 3. 19. Client For Microsoft Networks Windows 7 InfraredNAT Traversal is now widely implemented in routers and appliances. The. Green. Bow VPN Client supports NAT T drafts 1, 2 and 3 include udp encapsulation. Tunnel versus Transport Modes The differences between Transport mode and Tunnel mode can be defined www. RFC 2. 40. 1 thought. Tunnel Mode is most commonly used whenever either end of a security association is a. Tunnel mode encrypts both payload and the whole header. UDPTCP and IP. Transport Mode is used where traffic is destined for a security gateway and the security. SNMP commands. Transport Mode encrypts only the data portion and. IP header untouched. The. Green. Bow VPN Client supports both modes. Pre shared key versus Certificates Computer authentication by IPSec is performed by using preshared keys or computer certificates. A pre shared key identifies one party during Authentication Phase. Per definition, Pre shared. VPN tunnel. The strongest method of authentication is the use of a PKI and certificates. However, smaller organizations. PKI system and a well managed preshared key method can be easier and. The. Green. Bow VPN Client supports both modes. IPSec versus SSLPlease see our IPSec versus SSL page where we compare both technologies. What is DPD DPD or Dead Peer Detection is an Internet Key Exchange IKE extension i. RFC3. 70. 6. for detecting a dead IKE peer. This mechanism is used by the Redundant Gateway feature. Can Dead Peer Detection DPD be disabled Yes. A new checkbox appeared in VPN Client release 5. DPD easily. Go to the. Configuration Panel Global Parameters then uncheck the Dead Peer Detection DPD checkbox. The. Green. Bow VPN Client software. Which Windows versions are supported Releases which support old Windows versions Have also a look at the VPN Client for Android. Which languages are supported The. Green. Bow VPN Client is now available in many languages e. English, French, German, Portuguese, Spanish,. Check our supported languages list, increasing daily, to find your language. The language can be selected during software installation of the VPN Client. How to localize the VPN Client Do you want to have The. Green. Bow VPN Client in your own language Go to VPN Client localization. VPN Client strings file. The localization process is very simple and the translation in your language will be available on our next release. Which are the compatible GatewaysThe. Green. Bow VPN Client is compatible with all IPSec routers compliant to the existing standards IKE IPsec. Check our Certified VPN Products list, increasing daily, to find your VPN gateway. If the equipment you are looking for is not contained in this list, please contact our tech support. We will need configuration file, log file from Console window. How to connect the VPN Client to Linksys VPN routerWeve made available for download VPN Configuration Guides for most of the gateways we support on our web site. Linksys. VPN Configuration Guides are either written by our partners. We do support Linksys RV0. Linksys BEFVP4. 1. You might want to look at our answer about Linksys WRV5. G. How to setup The. Green. Bow VPN Client using Cisco Weve made available for download VPN Configuration Guides for most of the. Cisco. VPN Configuration Guides are either written. We do support Cisco gateways like Cisco PIX5. Cisco ASA 5. 51. 0, Cisco PIX 5. E, Cisco 8. 71, Cisco 1. Do you support NAT Traversal Yes. We do support NAT Traversal Draft 1 enhanced, Draft 2 and 3 full implementation. IP address emulation. Including NATOA support. Including NAT keepalive. Including NAT T aggressive mode. Does The. Green. Bow VPN Client support DNSWINS discovering Yes, the VPN Client does support the Mode Config. Mode Config is an Internet Key Exchange. IKE extension that enables the IPSec VPN gateway to provide LAN configuration such as DNSWINS. Getting Rid Of Cracked Heels Naturally Slim. VPN Client. In case Mode Config is. DNS and WINS server IP addresses of the remote LAN can be defined. VPN Client, to help users to resolve intranet addressing. Is The. Green. Bow VPN Client compatible with Linksys WRV5. G The. Green. Bow VPN Client is fully compatible and qualified with Linksys WRV5. G firmware 2. 3. 7 and later. Please download Linksys WRV5. G VPN Configuration Guide. The Linksys WRV5. G firmware 2. 2. 5. IPSec connexions from any VPN Clients with. IP addresses. However, there is a workaround. You need to set up VPN Clients IP address. Linksys configuration. Linksys has released a newer firmware since then. You might want to. The. Green. Bow VPN Client is fully compatible and qualified with Linksys RV0. Linksys BEFVP4. 1. Compatible VPN Products list or download VPN. Configuration Guides. Which port is needed by The. Green. Bow VPN Client UDP port 5. UDP port 4. ESP protocol protocol number 5. See also other FAQs Is it possible to use The. Green. Bow VPN Client through Microsoft ISA Server 2. According from Microsoft support, in most cases, IPSec VPN traffic does not pass through ISA Server 2. For more details about ISA server 2. Q8. 38. 37. 9 in Microsoft Knowledge Base. What must be filled in Phase 2 field VPN client addressThis field is the virtual IP address that the VPN Client will have inside the remote subnet. With most of VPN gateways. For example, if you use a VPN gateway with a subnet 1. VPN Client address. Take the case you choose an IP address non used in the subnet like 1.
A RIS Disc image went out that did not have File and Print Sharing for Microsoft Networks turned on Oh NO Now I want to fix it with a script deployed. This article shows how make Cisco VPN Client work with Windows 8 32bit 64bit. VPN Client including 5. VPN networks due. Component Description Supported by Active Directory A set of technologies introduced with Windows 2000 that allows administrators to assign enterprisewide policies. Client For Microsoft Networks Windows 7 Info' title='Client For Microsoft Networks Windows 7 Info' />A virtual private network VPN is a way to use a public telecommunication infrastructure. Internet, to provide remote offices or individual users with secure access to. In the past, companies would have rented expensive systems of leased lines to build. VPN only they could use. A VPN provides the same capabilities at a much lower cost. A VPN works by using the Internet while maintaining privacy through security procedures and. Windows 98 codenamed Memphis while in development is a graphical operating system by Microsoft. It is the second major release in the Windows 9x line of operating. Layer Two Tunneling Protocol L2. TP or IPSec. In effect, private data. Why IPSec is strong Definition IPSec Internet Protocol Security provides security services at the IP layer. The IPsec architecture is described in the RFC 2. RFC 2. 40. 1. IPSec has been selected to be embedded in IPv. IPSec is strong because it was designed to be. PPTP. Today IPSec is the most secure way to access the corporate network from the Internet, here are some elements why Strong encryption mechanisms like Encapsulated Security Payload ESP using DES, 3. DES, AES with long key length i. Strong authentication of parties identity with the use of X Auth and Certificate with long key length i. Use of Internet Key Exchange IKE and ISAKMP to automatically exchange keys and mutual authentication. Protection against denial of service attacks. The IPSec protocols use a sliding window. Packets are numbered and only accepted if they fit the window. Use of USB Stick, USB Token in conjunction with IPSec Client software to protect identityauthentication information and VPN configurations i. The. Green. Bow specific feature. What is NAT Traversal and do you support itDefinition Network Address Translation NAT is designed to decrease IT manager frustration for. IP addresses. A NAT device takes a packets originating private IP address. IP address, before sending the packet across the Internet. NAT devices use an internal table to keep track of translated addresses but. IP header, impacting IPSec ability to function. IETF Internet Engineering Task Force group worked out a solution called NAT Traversal. NAT T RFC 3. 19. Client For Microsoft Networks Windows 7 InfraredNAT Traversal is now widely implemented in routers and appliances. The. Green. Bow VPN Client supports NAT T drafts 1, 2 and 3 include udp encapsulation. Tunnel versus Transport Modes The differences between Transport mode and Tunnel mode can be defined www. RFC 2. 40. 1 thought. Tunnel Mode is most commonly used whenever either end of a security association is a. Tunnel mode encrypts both payload and the whole header. UDPTCP and IP. Transport Mode is used where traffic is destined for a security gateway and the security. SNMP commands. Transport Mode encrypts only the data portion and. IP header untouched. The. Green. Bow VPN Client supports both modes. Pre shared key versus Certificates Computer authentication by IPSec is performed by using preshared keys or computer certificates. A pre shared key identifies one party during Authentication Phase. Per definition, Pre shared. VPN tunnel. The strongest method of authentication is the use of a PKI and certificates. However, smaller organizations. PKI system and a well managed preshared key method can be easier and. The. Green. Bow VPN Client supports both modes. IPSec versus SSLPlease see our IPSec versus SSL page where we compare both technologies. What is DPD DPD or Dead Peer Detection is an Internet Key Exchange IKE extension i. RFC3. 70. 6. for detecting a dead IKE peer. This mechanism is used by the Redundant Gateway feature. Can Dead Peer Detection DPD be disabled Yes. A new checkbox appeared in VPN Client release 5. DPD easily. Go to the. Configuration Panel Global Parameters then uncheck the Dead Peer Detection DPD checkbox. The. Green. Bow VPN Client software. Which Windows versions are supported Releases which support old Windows versions Have also a look at the VPN Client for Android. Which languages are supported The. Green. Bow VPN Client is now available in many languages e. English, French, German, Portuguese, Spanish,. Check our supported languages list, increasing daily, to find your language. The language can be selected during software installation of the VPN Client. How to localize the VPN Client Do you want to have The. Green. Bow VPN Client in your own language Go to VPN Client localization. VPN Client strings file. The localization process is very simple and the translation in your language will be available on our next release. Which are the compatible GatewaysThe. Green. Bow VPN Client is compatible with all IPSec routers compliant to the existing standards IKE IPsec. Check our Certified VPN Products list, increasing daily, to find your VPN gateway. If the equipment you are looking for is not contained in this list, please contact our tech support. We will need configuration file, log file from Console window. How to connect the VPN Client to Linksys VPN routerWeve made available for download VPN Configuration Guides for most of the gateways we support on our web site. Linksys. VPN Configuration Guides are either written by our partners. We do support Linksys RV0. Linksys BEFVP4. 1. You might want to look at our answer about Linksys WRV5. G. How to setup The. Green. Bow VPN Client using Cisco Weve made available for download VPN Configuration Guides for most of the. Cisco. VPN Configuration Guides are either written. We do support Cisco gateways like Cisco PIX5. Cisco ASA 5. 51. 0, Cisco PIX 5. E, Cisco 8. 71, Cisco 1. Do you support NAT Traversal Yes. We do support NAT Traversal Draft 1 enhanced, Draft 2 and 3 full implementation. IP address emulation. Including NATOA support. Including NAT keepalive. Including NAT T aggressive mode. Does The. Green. Bow VPN Client support DNSWINS discovering Yes, the VPN Client does support the Mode Config. Mode Config is an Internet Key Exchange. IKE extension that enables the IPSec VPN gateway to provide LAN configuration such as DNSWINS. Getting Rid Of Cracked Heels Naturally Slim. VPN Client. In case Mode Config is. DNS and WINS server IP addresses of the remote LAN can be defined. VPN Client, to help users to resolve intranet addressing. Is The. Green. Bow VPN Client compatible with Linksys WRV5. G The. Green. Bow VPN Client is fully compatible and qualified with Linksys WRV5. G firmware 2. 3. 7 and later. Please download Linksys WRV5. G VPN Configuration Guide. The Linksys WRV5. G firmware 2. 2. 5. IPSec connexions from any VPN Clients with. IP addresses. However, there is a workaround. You need to set up VPN Clients IP address. Linksys configuration. Linksys has released a newer firmware since then. You might want to. The. Green. Bow VPN Client is fully compatible and qualified with Linksys RV0. Linksys BEFVP4. 1. Compatible VPN Products list or download VPN. Configuration Guides. Which port is needed by The. Green. Bow VPN Client UDP port 5. UDP port 4. ESP protocol protocol number 5. See also other FAQs Is it possible to use The. Green. Bow VPN Client through Microsoft ISA Server 2. According from Microsoft support, in most cases, IPSec VPN traffic does not pass through ISA Server 2. For more details about ISA server 2. Q8. 38. 37. 9 in Microsoft Knowledge Base. What must be filled in Phase 2 field VPN client addressThis field is the virtual IP address that the VPN Client will have inside the remote subnet. With most of VPN gateways. For example, if you use a VPN gateway with a subnet 1. VPN Client address. Take the case you choose an IP address non used in the subnet like 1.